Following on from previous posts about my new pfSense device I’m going to write a quick guide on how to add authorised SSH keys to a user account so one can move away from password based authentication when connecting over Secure Shell (SSH).
There are many clients available for SSH connectivity and key generation, I am only going to use PuTTy and it’s ‘Key Generator’ tool as an example in this post as the software is freely available and commonly used.
PuTTY Download
First off you will need to get the PuTTY files – these are available at the following link –
http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html
PuTTY Key Generator Tool
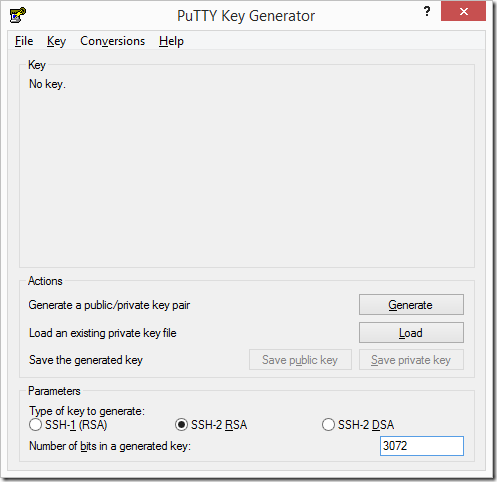
Having downloaded and launched the PuTTY Key Generator tool we first have to select what type of key to generate along with a key size. SSH-2 RSA is strongly recommended as the key type. In terms of key size it is important to understand that a larger key provides ‘extra’ security at the cost of processing overhead. These days a 2048 bit key is sufficient however if you do wish to use a larger key then 3072 or 4096 bits should be plenty. If you are configuring within a corporate environment please consult with your governance/security colleagues to understand what policies or legislation may be in place that stipulates a key size.
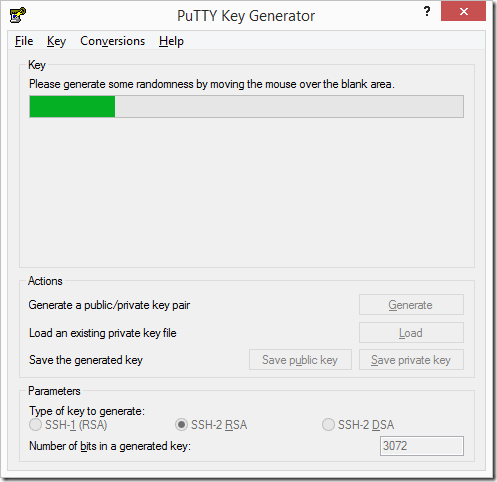
Having selected the appropriate options click on the ‘Generate‘ button, this will begin the key creation process. The program will request you move the mouse randomly within the box to add additional entropy.
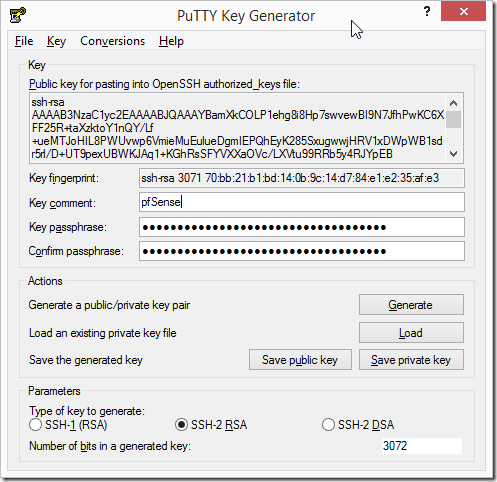
Once the key pair has been created we have the option to add a passphrase as well as save the public and private keys. Personally I would recommend adding a strong (i.e long and complex) passphrase to your private key. This will result in the key being encrypted and only usable to somebody with the correct passphrase. Not adding one would mean if somebody got hold of your private key they would be able to connect to systems configured with your public key – not a good thing.
When saving the private key I would also recommend you think carefully about where to store it – I know one person who keeps their private keys on an encrypted USB memory stick. This allows him to carry them around while also keeping them safe via the AES full disk encryption on the stick itself. Having decided on a location save the private key and you can also save a copy of the public key.
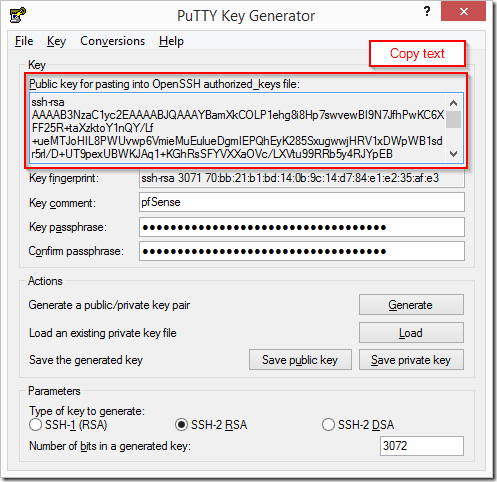
Do not close the PuTTY window – copy the text in the top box in it’s entirety, we will be pasting this into our user account on the pfSense web console.
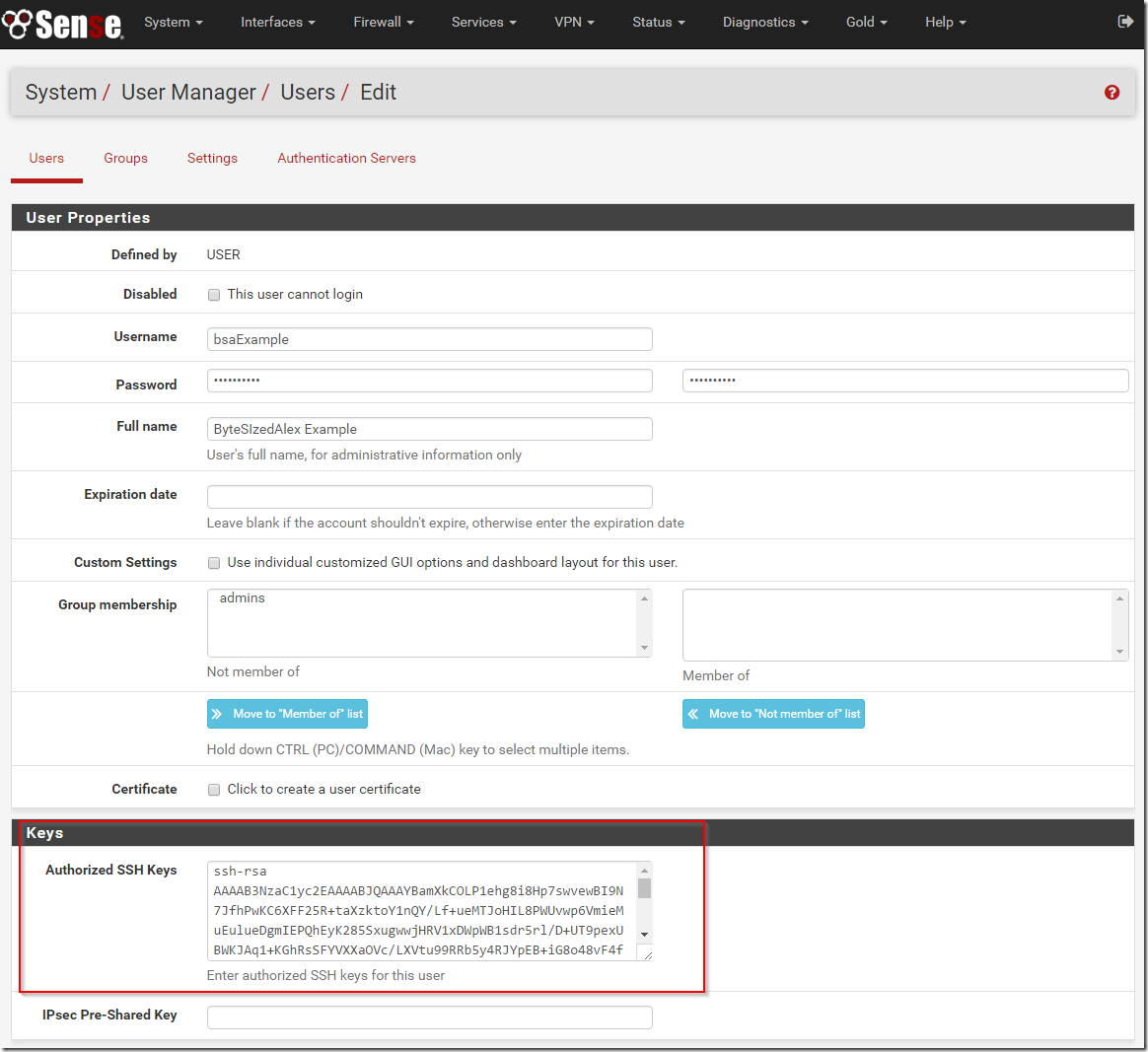
pfSense User Account Authorised SSH Keys Configuration
We can now configure our user account with the newly created SSH key. In this example I’m creating a new user and adding the SSH PUBLIC key to the authorised SSH keys section. I know many people will be aware that you need to paste in the public key but I have seen this mistake made before.
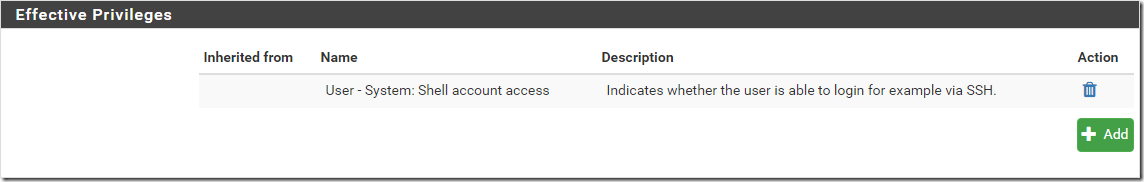
You may also need to assign a custom privilege to the user account – this will depend on whether you made it an administrator or added to a group with the require access.
Now that we have configured the user account we can try to connect using our SSH keys with PuTTY.
PuTTY Connection
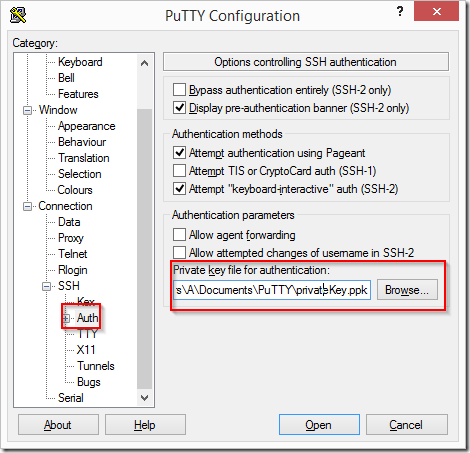
PuTTY needs to be configured with the private key, to do this navigate to –
- Connection –> SSH –> Auth
Click on the Browse button and select the private key file saved earlier. I am aware of programs like PAGEANT which we can use to manage keys but right now let’s just keep it simple.
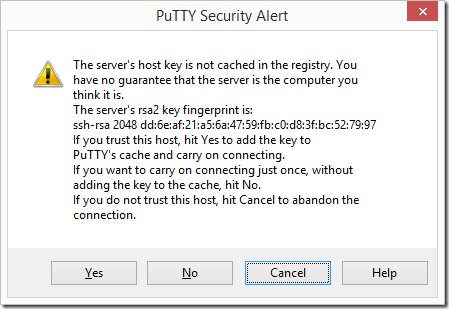
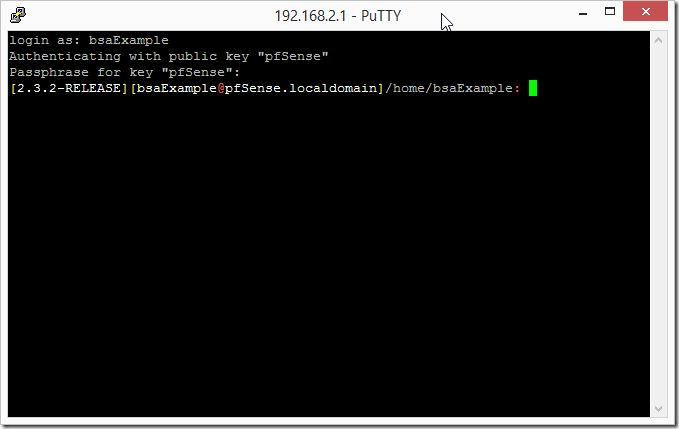
As this is my first time connecting I am presented with a warning for the pfSense RSA fingerprint.
I saved my private key with a passphrase so it prompts me for this after entering the username. Assuming everything is configured correctly we should get a shell prompt as demonstrated below.
Public key authentication is far more secure than a traditional password based model – I highly recommend you consider deploying this for any user who needs SSH shell access. There are also many other tools which can make life easier when handling keys however they will likely have a post of their own, so look out for these in the future.
Note in this post I make the assumption you are connecting from an interface/subnet which is allowed access on the SSH port, e.g a LAN interface. By default pfSense does not allow SSH access from the WAN side. If for some reason you do need SSH access externally I would recommend you consider creating a VPN (IPsec, OpenVPN etc.) in pfSense first and connect to this then tunnel your SSH session through the VPN.
Hopefully the above is useful to you – any questions or feedback drop them in the comments section below.
Me I tested with ssh keys from 2 yubikeys(windows/gpg keys moved to yubikey and exported as ssh keys from gpg), it works great.and used mobaxterm, I prefer it over putty :)
Hi, when I try to use the key it just gives me a Windows error sound when I press “Open” in SSH -> Auth
If you’re running Windows 10 or newer you should be able to take advantage of native SSH on the terminal. I’m guessing permissions are fine and you’ve tried running as admin to rule anything like that out?
I’ll have to try and reproduce the issue but any extra info you have would be great.