I rarely write articles on security or ‘hacking’ even though this is an area I have a great deal of interest in – unfortunately work often pulls me in other directions. Today I thought I’d start with something basic which may interest readers and then perhaps future articles will build on this.
Let us begin with finding Wi-Fi networks in range using a great suite of tools in the Aircrack-ng arsenal. If you would like to read more about the tools used in this post then check out the following link –
Wireless networking is taken for granted these days and though it had a bit of a rocky start security wise it’s certainly matured and is not quite as ‘Swiss cheese’ like as it once was. Throughout this post I will be making use of the Kali Linux distribution which is fantastic and full to the brim with amazing utilities, link to the home page below.
My assumption is you have Kali setup and a supported wireless adapter connected and working…
Now that we’ve got that out of the way let us begin.
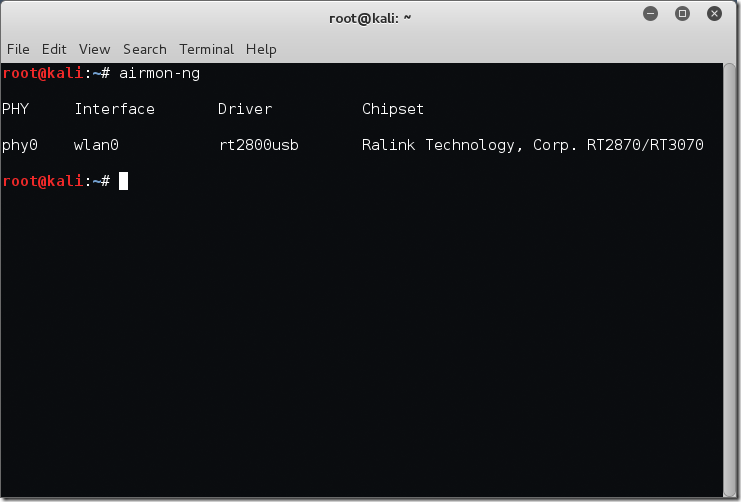
First off I’m going to run airmon-ng at the terminal to see what physical Wi-Fi adapters the system has picked up.
root@kali:~# airmon-ng
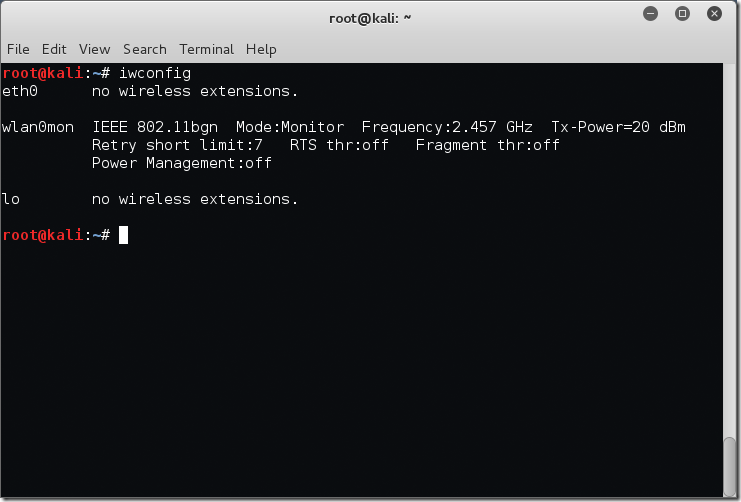
We can also leverage iwconfig to display the wireless interfaces – note I am not currently connected to any networks at this point.
root@kali:~# iwconfig eth0 no wireless extensions. wlan0 IEEE 802.11bgn ESSID:off/any Mode:Managed Access Point: Not-Associated Tx-Power=20 dBm Retry short limit:7 RTS thr:off Fragment thr:off Encryption key:off Power Management:off lo no wireless extensions. root@kali:~#
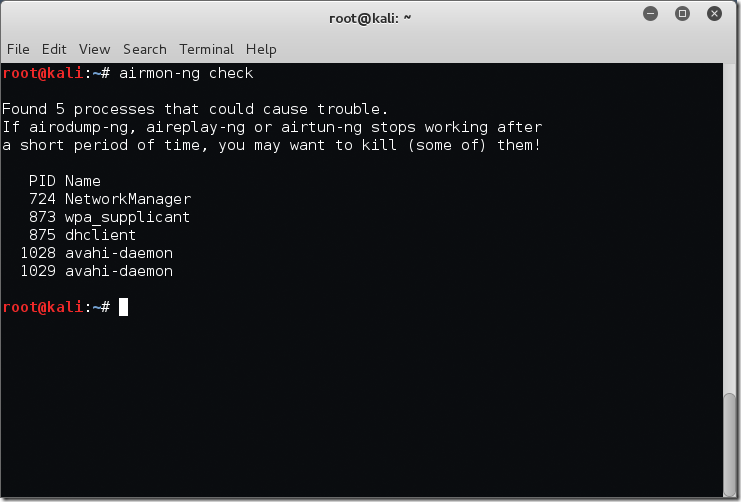
The next step is to check our system for any processes which may interfere with our tools and the setting change from ‘Managed’ mode to ‘Monitor’ mode. We will do this with the airmon-ng check command.
root@kali:~# airmon-ng check Found 5 processes that could cause trouble. If airodump-ng, aireplay-ng or airtun-ng stops working after a short period of time, you may want to kill (some of) them! PID Name 724 NetworkManager 873 wpa_supplicant 875 dhclient 1028 avahi-daemon 1029 avahi-daemon root@kali:~#
In my case there are 5 processes which may cause a problem. We definitely need to kill off the ‘NetworkManager’ process or it will interfere, usually doing things like changing the mode of the adapter back to ‘Managed’. For more in depth information feel free to refer to the airmon-ng wiki page here.
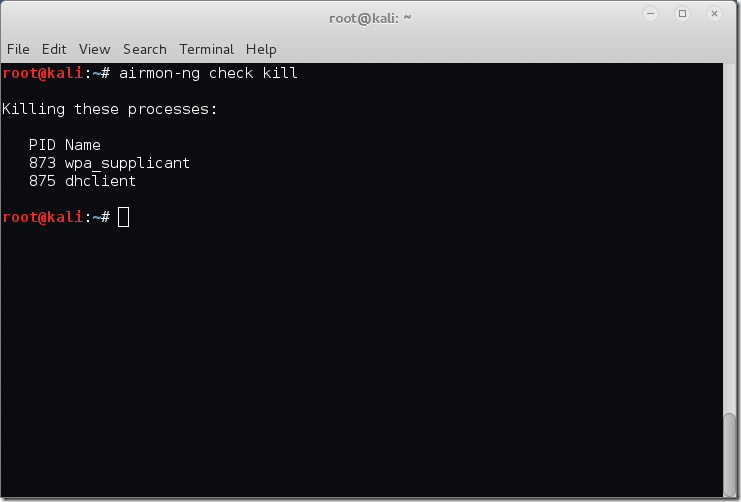
The easiest way to get rid of these processes is to use the airmon-ng check kill command. This will stop any network managers and then kill remaining processes.
root@kali:~# airmon-ng check kill Killing these processes: PID Name 873 wpa_supplicant 875 dhclient root@kali:~#
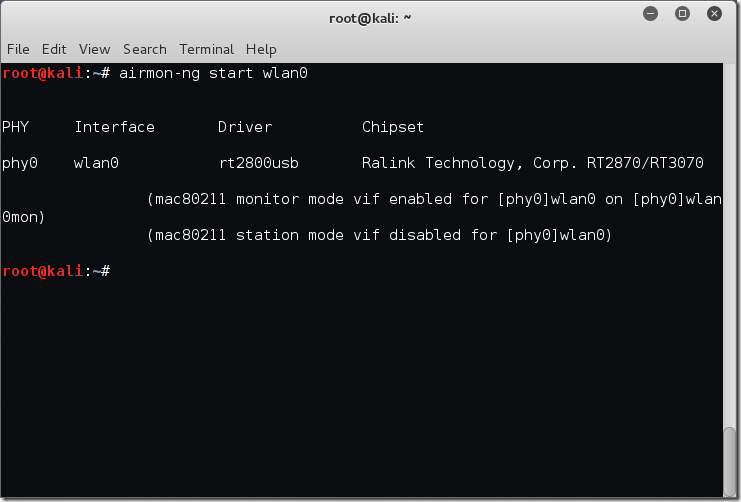
Now that we have taken care of network managers and processes it’s time to actually enable ‘Monitor’ mode on our wireless interface. To do this we will use the airmon-ng start [interfaceName] command. For me this will result in airmon-ng start wlan0 as below.
root@kali:~# airmon-ng start wlan0 PHY Interface Driver Chipset phy0 wlan0 rt2800usb Ralink Technology, Corp. RT2870/RT3070 (mac80211 monitor mode vif enabled for [phy0]wlan0 on [phy0]wlan0mon) (mac80211 station mode vif disabled for [phy0]wlan0) root@kali:~#
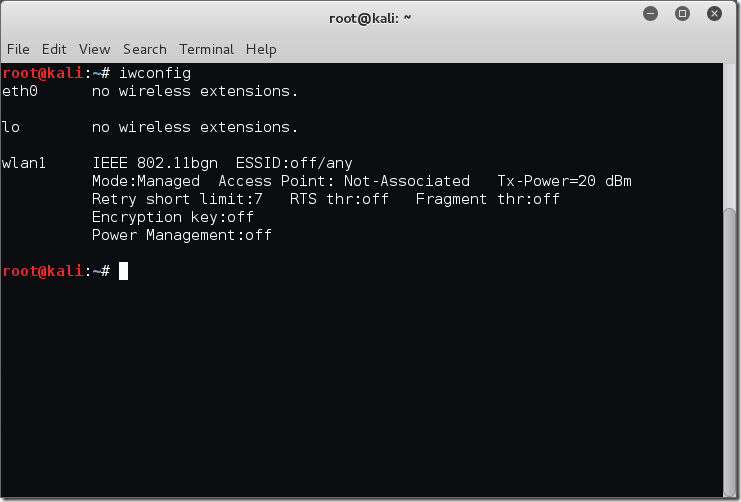
Now we are going to check that the interface is in the correct mode with the iwconfig command again.
root@kali:~# iwconfig eth0 no wireless extensions. wlan0mon IEEE 802.11bgn Mode:Monitor Frequency:2.457 GHz Tx-Power=20 dBm Retry short limit:7 RTS thr:off Fragment thr:off Power Management:off lo no wireless extensions. root@kali:~#
Excellent! We see that the interface is now listed in ‘Monitor’ mode.
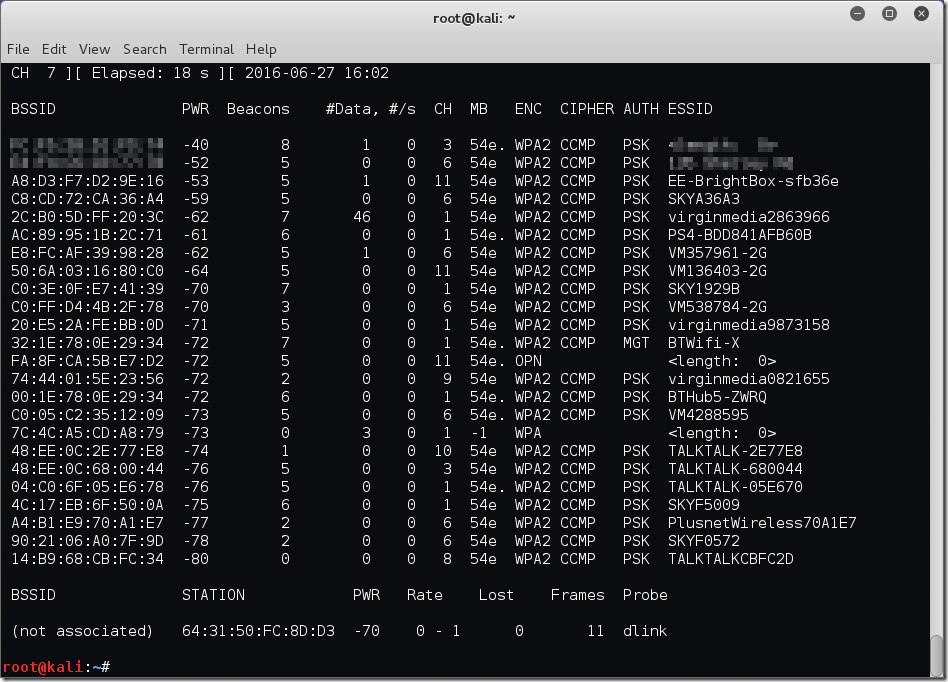
OK I know that was a lot of screenshots and text but it’s worth it trust me. Finally we are going to jump over to another tool in the Aircrack-ng suite called airodump-ng. In this case we are just going to use the basic syntax to show networks detected which is airmon-ng [interfaceName] as below.
root@kali:~# airodump-ng wlan0mon
As you can see a large number of networks have been detected – this was after 5 seconds of runtime before I killed airodump-ng. At this point we have a good overview of what is out there and within range of my antenna. The airodump-ng tool has a wide variety of switches which I’m not going to cover in this post, suffice to say future posts will delve a little deeper.
One thing I do find interesting in this screenshot is that a year or two back there would have been a few WEP encrypted networks in the mix but these days it’s becoming quite rare which is great for security but not so good if you were looking to crack the network.
Of course it goes without saying you should only be trying to crack a network you own or have legal permission to do so as part of a vulnerability assessment or penetration test.
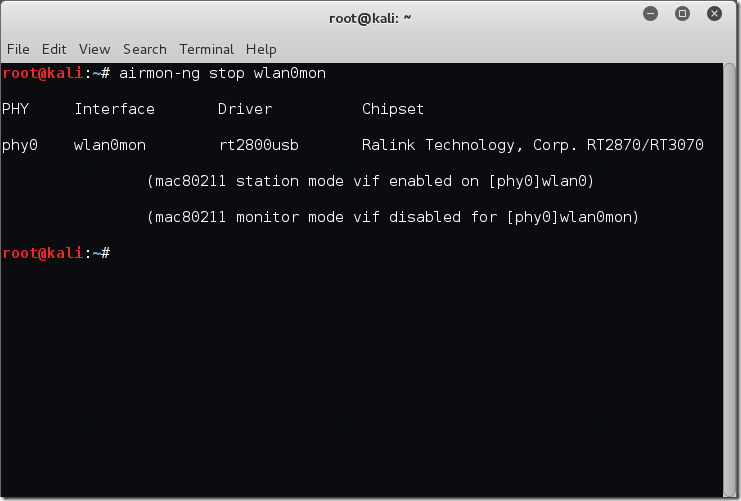
Once you have finished playing with airodump-ng you may be wondering how to return your wireless interface to ‘Managed’ mode. This is simple, again we leverage airmon-ng. In this case we will use the stop switch as below.
root@kali:~# airmon-ng stop wlan0mon PHY Interface Driver Chipset phy0 wlan0mon rt2800usb Ralink Technology, Corp. RT2870/RT3070 (mac80211 station mode vif enabled on [phy0]wlan0) (mac80211 monitor mode vif disabled for [phy0]wlan0mon) root@kali:~#
This post has remained intentionally basic and is merely a brief introduction to some of these tools, look forward to future posts covering things like attacking a WEP network (in case any still exist and for understanding) followed by things like WPA and enterprise environments. My hope is to make security posts a more regular thing, if my work allows!